MikroTik Dual WAN Load Balancing with Failover using PCC
Hi geek, going through this article means you are finding Load Balancing as well as Link Redundancy solution for your MikroTik network because you already have multiple WAN connections or you are planning to lease multiple WAN connections. MikroTik has various Load Balancing and Link Redundancy methods such as ECMP, PCC and so on. ECMP method provides an easy configurable load balancing with failover solution but it has some known issues too in a large network. On the hand, PCC provides 100% reliable load balancing and link redundancy solution but the configuration is a little bit complex. In my previous article I discussed how to easily configure ECMP Load Balancing and Link Redundancy network and in this article I will discuss how to configure PCC Load Balancing and Link Redundancy network with MikroTik Router over Dual Gateway.
Core Devices and IP Information
To configure a load balancing with failover network, I am using MikroTik RouterOS v6.38.1 that has two ISP connections and a LAN network. IP information that I am using for this network configuration are given below.
- ISP1 IP 192.168.30.2/30 and Gateway IP 192.168.30.1
- ISP2 IP 192.168.60.2/30 and Gateway IP 192.168.60.1
- LAN network: 10.10.70.0/24 and LAN Gateway IP 10.10.70.1/24
- DNS IP: 8.8.8.8 and 8.8.4.4
This IP information is just for my RND purpose. Change this information according to your network requirements.
Network Diagram
To configure a Load Balancing and Link Redundancy network with MikroTik RouterOS, I am following a network diagram like below image.
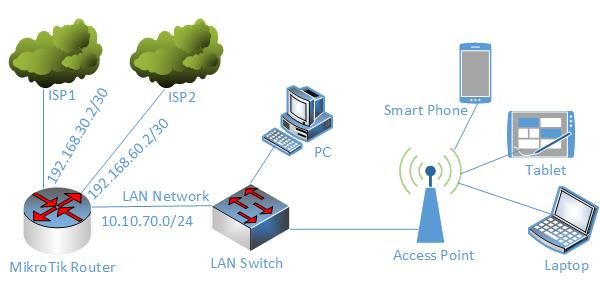
In this network, MikroTik Router’s 1st Interface (ether1) is connected to ISP1 having IP Address 192.168.30.2/30 and 2nd Interface (ether2) is connected to ISP2 having IP Address 192.168.60.2/30. In real network these IP Addresses should replace with your ISP given public IP Address. Again, 3rd Interface (ether3) is connected to LAN having IP network 10.10.70.0/24.
We will configure Dual WAN Load Balancing and Link Redundancy in this MikroTik Router using PCC method and after PCC configuration MikroTik will pass LAN traffic through both ISP equally and if any ISP is disconnected, other ISP will be used to pass all traffic until the disconnected ISP becomes alive. If disconnected ISP becomes alive, both ISP will be used to pass LAN traffic again automatically.
How PCC Works
PCC (Per Connection Classifier) uses hash function to divide traffics. Hash function has many interesting properties, but only one that is used for PCC method is that hash function is deterministic. That means if same input is given to hash function, it always generates same output. For example, if we provide a specific IP address to hash function multiple times, it always generates a specific integer value as its output.
PCC first feeds selected fields (src-address, dst-address, src-port, dst-port or any combination of these) from IP header to hash function and with the help of hashing algorithm converts selected fields into 32 bit integer value and divides the integer value with a given integer number and then marks any connection according to the remainder value. For example, the hash function is fed 1.1.1.1 as the source IP address, 10000 as the source TCP port, 2.2.2.2 as the destination IP address and 80 as the destination TCP port. The output will be 1+1+1+1+10000+2+2+2+2+80 = 10092. PCC now divides this output with a given integer value (if Dual WAN, integer value will be 2) and then marks connection according the remainder value such as if remainder is 0, connection is marked as 1st connection and if remainder is 1, connection is marked as 2nd connection.
PCC itself has absolutely nothing to do with routing, routing marks or spreading load. PCC is simply a way to match packets and to mark packets. Routing decision is taken by Policy Routing according to marked packet.
The following three rules and their explanation will show PCC packet marking more easily.
/ip firewall mangle add chain=prerouting action=mark-connection \new-connection-mark=1st_conn per-connection-classifier=src-address-and-port:3/0
/ip firewall mangle add chain=prerouting action=mark-connection \
new-connection-mark=2nd_conn per-connection-classifier=src-address-and-port:3/1
/ip firewall mangle add chain=prerouting action=mark-connection \
new-connection-mark=3rd_conn per-connection-classifier=src-address-and-port:3/2
The first line means produce the output of the hash function given the packet’s source IP address and port, divide it by 3 and if the remainder is 0, perform the action of marking the connection as 1st_conn. The second line means produce the output of the hash function given the packet’s source IP address and port, divide it by 3 and if the remainder is 1, perform the action of marking the connection as 2nd_conn. Similarly, the third line means produce the output of the hash function given the packet’s source IP address and port, divide it by 3 and if the remainder is 2, perform the action of marking the connection as 3rd_conn.
MikroTik Load Balancing and Link Redundancy Configuration over Dual WAN using PCC
We will now configure PCC Load Balancing with failover according to our above network diagram. Complete configuration can be divided into the following four parts.
- MikroTik Router basic configuration
- Creating Mangle rule
- Policy based routing configuration
- NAT configuration
Part 1: MikroTik Router Basic Configuration
In the basic part, we will assign 1st WAN IP address given from ISP1, 2nd WAN IP address given from ISP2, LAN gateway and DNS. The following steps will show how to perform these steps in MikroTik Router.
- Login to MikroTik Router with winbox by admin privilege credential.
- Click on Interfaces menu item. Interface List window will appear.
- Double click on ether1 interface and rename it as ISP1 and then click Apply and OK button. Similarly, click on ether2 interface and rename it as ISP2 and then click Apply and OK button. Again, click on ether3 interface and rename it as LAN and then click Apply and OK button.
- Go to IP > Addresses menu item and click on PLUS SIGN (+). In New Address window, put ISP1 IP address (192.168.30.2/30) in Address input field and choose ISP1 from Interface dropdown menu and then click on Apply and OK button.
- Similarly, click on PLUS SIGN (+). In New Address window, put ISP2 IP address (192.168.60.2/30) in Address input field and choose ISP2 from Interface dropdown menu and then click on Apply and OK button.
- Again, click on PLUS SIGN (+). In New Address window, put LAN Gateway IP address (10.10.70.1/24) in Address input field and choose LAN from Interface dropdown menu and then click on Apply and OK button.
- Go to IP > DNS menu item and put DNS IP (8.8.8.8) in Servers input field and click Apply and OK button.
Alternatively, you can run below command from MikroTik CLI.
/interfaceset “ether1″ name=”ISP1”
set “ether2″ name=”ISP2”
set “ether3″ name=”LAN”
/ ip address
add address=192.168.30.2/30 interface=ISP1
add address=192.168.60.2/30 interface=ISP2
add address=10.10.70.1/24 interface=LAN
MikroTik Router basic configuration has been completed. Now we will create Mangle rule to mark connection and routing.
Part 2: Creating Mangle Rule
Mangle rule is used to mark packet for proper routing. In this part we will create various mangle rules that will help to mark connection and routing and pass different network traffics to different WAN connections. Go to IP > Firewall menu item and click on Mangle tab and create the following 10 rules as indicated.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and put ISP1 network address (192.168.30.0/30) in Dst. Address input and then choose LAN from In. Interface dropdown menu. Now click on Action tab and choose accept from Action dropdown menu and then click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and put ISP2 network address (192.168.60.0/30) in Dst. Address input and then choose LAN from In. Interface dropdown menu. Now click on Action tab and choose accept from Action dropdown menu and then click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and choose ISP1 from In. Interface dropdown menu and then choose no-mark from Connection Mark dropdown menu. Now click on Action tab and choose mark connection from Action dropdown menu and put a connection mark name (ISP1_conn) in New Connection Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and choose ISP2 from In. Interface dropdown menu and then choose no-mark from Connection Mark dropdown menu. Now click on Action tab and choose mark connection from Action dropdown menu and put a connection mark name (ISP2_conn) in New Connection Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and choose LAN from In. Interface dropdown menu and then choose no-mark from Connection Mark dropdown menu. Click on Advanced tab and choose both addresses from Per Connection Classifier dropdown menu and put 2 in next 1st input field and 0 in 2nd input field. Click on Extra tab and click on Dst. Address Type option and choose local from Address Type dropdown menu and then click on Invert checkbox. Click on Action tab and choose mark connection from Action dropdown menu and put a connection mark name (ISP1_conn) in New Connection Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and choose LAN from In. Interface dropdown menu and then choose no-mark from Connection Mark dropdown menu. Click on Advanced tab and choose both addresses from Per Connection Classifier dropdown menu and put 2 in next 1st input field and 1 in 2nd input field. Click on Extra tab and click on Dst. Address Type option and choose local from Address Type dropdown menu and then click on Invert checkbox. Click on Action tab and choose mark connection from Action dropdown menu and put a connection mark name (ISP2_conn) in New Connection Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and choose LAN from In. Interface dropdown menu and then choose ISP1_conn from Connection Mark dropdown menu. Now click on Action tab and choose mark routing from Action dropdown menu and put a routing mark name (to_ISP1) in New Routing Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose prerouting from Chain dropdown menu and choose LAN from In. Interface dropdown menu and then choose ISP2_conn from Connection Mark dropdown menu. Now click on Action tab and choose mark routing from Action dropdown menu and put a routing mark name (to_ISP2) in New Routing Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose output from Chain dropdown menu and then choose ISP1_conn from Connection Mark dropdown menu. Now click on Action tab and choose mark routing from Action dropdown menu and put a routing mark name (to_ISP1) in New Routing Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
- Click on PLUS SIGN (+). New Mangle Rule window will appear. Click on General tab and choose output from Chain dropdown menu and then choose ISP2_conn from Connection Mark dropdown menu. Now click on Action tab and choose mark routing from Action dropdown menu and put a routing mark name (to_ISP2) in New Routing Mark input field. Uncheck Passthrough checkbox if it is checked. Click on Apply and OK button.
Alternatively, you can run below command from MikroTik CLI.
/ ip firewall mangleadd chain=prerouting dst-address=192.168.30.0/30 action=accept in-interface=LAN
add chain=prerouting dst-address=192.168.60.0/30 action=accept in-interface=LAN
add chain=prerouting in-interface=ISP1 connection-mark=no-mark action=mark-connection \
new-connection-mark=ISP1_conn
add chain=prerouting in-interface=ISP2 connection-mark=no-mark action=mark-connection \
new-connection-mark=ISP2_conn
add chain=prerouting in-interface=LAN connection-mark=no-mark dst-address-type=!local \
per-connection-classifier=both-addresses:2/0 action=mark-connection new-connection-mark=ISP1_conn
add chain=prerouting in-interface=LAN connection-mark=no-mark dst-address-type=!local \
per-connection-classifier=both-addresses:2/1 action=mark-connection new-connection-mark=ISP2_conn
add chain=prerouting connection-mark=ISP1_conn in-interface=LAN action=mark-routing \
new-routing-mark=to_ISP1
add chain=prerouting connection-mark=ISP2_conn in-interface=LAN action=mark-routing \
new-routing-mark=to_ISP2
add chain=output connection-mark=ISP1_conn action=mark-routing new-routing-mark=to_ISP1
add chain=output connection-mark=ISP2_conn action=mark-routing new-routing-mark=to_ISP2
Mangle rules for matching and marking packets has been created successfully. Now we will configure policy based routing so that marked packet can be routed properly through appropriate ISP connection.
Part 3: Policy Based Routing Configuration
Mangle rules that we have created will mark connection but do not do anything in routing. To pass marked connection to appropriate ISP connection, we need to configure policy based routing. The following steps will show how to configure policy based routing for the marked connection.
- Go to IP > Routes menu item. Route List window will appear.
- Click on PLUS SIGN (+). New Route window will appear. Put ISP1 gateway address (192.168.30.1) in Gateway input field. Choose ping from Check Gateway dropdown menu. Choose ISP1 routing mark (to_ISP1) from Routing Mark dropdown menu. Click Apply and OK button.
- Click on PLUS SIGN (+). New Route window will appear. Put ISP2 gateway address (192.168.60.1) in Gateway input field. Choose ping from Check Gateway dropdown menu. Choose ISP2 routing mark (to_ISP2) from Routing Mark dropdown menu. Click Apply and OK button.
- Click on PLUS SIGN (+). New Route window will appear. Put ISP1 gateway address (192.168.30.1) in Gateway input field. Choose ping from Check Gateway dropdown menu. Put 1 in Distance input field and Click Apply and OK button.
- Click on PLUS SIGN (+). New Route window will appear. Put ISP2 gateway address (192.168.60.1) in Gateway input field. Choose ping from Check Gateway dropdown menu. Put 2 in Distance input field and Click Apply and OK button.
Alternatively, you can run below command from MikroTik CLI.
/ ip routeadd dst-address=0.0.0.0/0 gateway=192.168.30.1 routing-mark=to_ISP1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.60.1 routing-mark=to_ISP2 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.30.1 distance=1 check-gateway=ping
add dst-address=0.0.0.0/0 gateway=192.168.60.1 distance=2 check-gateway=ping
Routing configuration for selecting proper ISP has been completed. Now we need to configure NATing so that LAN traffic can reach to internet.
Part 4: NAT Configuration
In last part, we will configure NATing. Otherwise LAN user cannot reach to internet through MikroTik Router. The following steps will guide how to configure NAT in MikroTik Router for a specific ISP connection.
- Go to IP > Firewall menu item and click on NAT tab.
- Click on PLUS SIGN (+). New NAT Rule window will appear. In General tab, choose srcnat from Chain dropdown menu and choose ISP1 from Out. Interface dropdown menu. Click on Action tab and choose masquerade from Action dropdown menu and click Apply and OK button.
- Similarly, click on PLUS SIGN (+) again. New NAT Rule window will appear. In General tab, choose srcnat from Chain dropdown menu and choose ISP2 from Out. Interface dropdown menu. Click on Action tab and choose masquerade from Action dropdown menu and click Apply and OK button.
Alternatively, you can run below command from MikroTik CLI.
/ ip firewall natadd chain=srcnat out-interface=ISP1 action=masquerade
add chain=srcnat out-interface=ISP2 action=masquerade
NAT configuration as well as all our configurations for PCC Load Balancing and Link Redundancy has been completed. Now LAN user will get uninterrupted internet connection until both ISP connection is lost.
Follow the below video about MikroTik PCC Load Balancing and Link Redundancy if you face any confusion to follow the steps. I hope it will reduce your any confusion.
MikroTik Dual WAN Load Balancing and Link Redundancy using PCC have been discussed in this article from very beginning. I hope you will now be able to configure a 100% reliable Load Balancing and Link Redundancy network with your MikroTik Router using PCC method. However, if you face any confusion to apply PCC method, feel free to discuss in comment or contact with me from Contact page. I will try my best to stay with you.
Why not a Cup of COFFEE if the solution?


Dear Sayeed Vai ,
Thanks for great sharing .You are doing a great job for us .
Br,
captor
Dear Sayeed,
It is very interesting article, other are also. I’ve did step by step but I’ve failed. I’ve no internet connection, and don’t know what is wrong.
I’d used hAP lite RB951 with 6,42 RouterOS, or RB962 with 6,42 RouterOS. I’ve go two ISP: one is radioline ISP, second is LTE gate (Huawei 5186 with HuigateOS). Separately both work perfectly – with autoconfig from Mikrotik.
Trying to bond it – I’ve failed.
Can You give me any suggestions?
Both ISP provide static public IP or other system? this article is just for static public IP. Follow my video that provides with this article and check your configuration.
Your Video Link Pls
Video is embedded with this article. Youtube link is also there.
hi,
How to do multiple isp failover if i dont use masquarade, i use src-nat ?
The basic without failover is like this, when theres no isp down, there is no problem
1 chain=srcnat action=src-nat to-addresses=x.x.x.101 src-address=10.10.1.0/24 log=no log-prefix=””
2 chain=srcnat action=src-nat to-addresses=y.y.y.101 src-address=10.25.1.0/24 log=no log-prefix=””
The problem is when link to gateway y.y.y. down or isp down, mikrotik still doing nat to the gateway.
If im doing this nat below, i can do a failover but manualy, by disable the down isp and clear the connection.
1 chain=srcnat action=src-nat to-addresses=x.x.x.101 src-address=10.10.1.0/24 log=no log-prefix=””
2 chain=srcnat action=src-nat to-addresses=y.y.y.101 src-address=10.25.1.0/24 log=no log-prefix=””
3 chain=srcnat action=src-nat to-addresses=y.y.y.101 src-address=10.10.1.0/24 log=no log-prefix=””
4 chain=srcnat action=src-nat to-addresses=x.x.x.101 src-address=10.25.1.0/24 log=no log-prefix=””
Thx.
src-nat is 1 to 1 relationship. So, I think it is not possible.
Hello there!
I have to different ISPs. For examle 194.29.62.118/24 gateway 194.29.62.1 – ISP1, 194.187.104.150/30 gateway 194.187.104.148 – ISP2. Both of them are static IPs. I need to make them work together balancing the output traffic. Both ISPs have 50Mbs speed. ISP1 connected to ether1, ISP2 connected to ether2, I can’t figure out how to make them work together on RB951G-2Hnd. Everything seemed to work fine following the configuration instruction founded in the Internet. BUT, I have an outside connection to ISP1 port 10000 that needs to be forwarded to local machine 192.168.88.100 on RDP port 4000. How to make all of that stuff working fine?
BTW, forgot to notice that I need machine with 192.168.88.100 to send packets & use only connection via ISP1.
You should make Mangle Rule to mark-connection coming from 192.168.88.100 and make a conditional routing to ISP1. For reference you can follow: https://systemzone.net/mikrotik-load-balancing-over-multiple-gateway-2-wan
Hello Sayeed,
Thanks a lot for sharing your work and tutorials.
I have two ISP, hAP lite router and 10/15 network clients.
I’ve tried load balancing via ECMP but had a lot of timeout errors, cerificate and so but load balancing was working, bot ISP were used to access to Internet.
Now since you’re telling that PCC works better I’ve tried it as well. But even after triple checking my configuration, failover works nicely but load balancing not at all, isp1 (wan_dsl) has full throttle and isp2 (wan_4G) isn’t used at all
http://prntscr.com/mu27ce
I’ve also tried to apply unequal wan via PCC, same results…
What do you think is happening here ?
are your mangle rule working properly? check or try the configuration to another routerOS. Also check the configuration with the mikrotik wiki https://wiki.mikrotik.com/wiki/Manual:PCC.