MikroTik Firewall Basic Concept
MikroTik Firewall functions as a network security tool for preventing unauthorized access to networks as well as provides Network Address Translation functionality. So, a network administrator who is using MikroTik Router in his network cannot go a single day without MikroTik Firewall. Actually, the main duty of a MikroTik administrator is to maintain Firewall properly along with Bandwidth management after completing MikroTik Router basic configuration. So, a MikroTik administrator should have enough knowledge on MikroTik Firewall and so this article is designed to discuss the basic concept on MikroTik Router Firewall.
MikroTik Firewall
MikroTik Firewall mainly filters good traffic or bad traffic and according to the definition of firewall it should allow good traffic and reject bad traffic. This good and bad traffic is doing one event among the following three events in MikroTik Router.
- Either the traffic is entering to MikroTik Router,
- The traffic is leaving from MikroTik Router or
- The traffic is passing through MikroTik Router.
MikroTik administrators like you and me always expect to get good traffic entering to and passing from our MikroTik Router. But the fact is not like so always. We have to always fight against bad traffics. When a local network is connected to public networks, there is always a threat that someone from outside of your local network will break into your local network. This security break may cause private data being stolen and distributed, valuable data being altered or destroyed, or entire hard drives being erased. MikroTik Firewall is used to prevent or minimize these types of security risk. MikroTik Firewall has a lot of firewalling features as well as masquerading capabilities that help to hide your private network from outside’s bad traffic.
The key features of MikroTik Firewall are able to inspect network packet, detect Layer-7 protocol and peer to peer protocols filtering. MikroTik firewall is also capable to classify network traffic by source MAC address, IP address, port or port range, IP protocols, interface the packet arrived from or left through, packet content, packet size, packet arrive time and much more.
By default, MikroTik Firewall allows all traffics that are entering to your router, leaving from your router or passing through your router. That means, initially MikroTik Router acts as an open firewall where there is no barrier and all traffics are considered as good traffic. So, if you feel any traffic is bad and need to block it, you have to apply MikroTik Firewall Rule.
What is MikroTik Firewall Rule?
MikroTik Firewall Rule is nothing but a meaningful statement that is used to allow good traffics or block bad traffics. Actually, MikroTik Firewall functions based on firewall rule. Then, what is in a firewall rule? There are two parts in a Firewall rule.
- The matcher or conditional part checks traffic flow against any given condition and
- The action part takes decision to do any activity with the matched condition.
Condition in MikroTik Firewall Rule
The conditional part of a firewall rule takes various property values that will be matched to apply any firewall rule. If you visit MikroTik Firewall with winbox software following IP > Firewall > Filter Rules instruction and click on PLUS SIGN (+) to create a new firewall rule, you will find General, Advanced and Extra tabs that combinedly make firewall conditions. A lot of property options or parameters are available in MikroTik Firewall’s conditional part. Most of the property options are self-defined but among these, chain parameter makes much complexity to a new MikroTik administrator. But it is not so complex if you try to understand deeply.
The Chain Property
There are three predefined chains in MikroTik Firewall rule.
- Input processes those packets which are entering to your MikroTik Router. These packets may come through any interface of your router. So, any packet that is coming to your MikroTik Router and containing MikroTik interface IP address as destination IP address is processed by input chain. In short, when MikroTik Router is destination then it is considered as input chain activity. For example, if you or anyone wants to connect to MikroTik Router with SSH or Winbox or wants to browse HTTP contents, the destination IP address will be MikroTik IP addresses. So, this is an input chain activity and if you want to block SSH or HTTP protocol, you have to select input chain in firewall rule.
- Output processes those packets which are originated from your MikroTik Router and leaving it through one of the MikroTik interfaces. So, the packet that is leaving from your router containing any interface IP address as source IP address is processed by output chain. In short, when MikroTik Router address is the packet source address then it is considered as output chain activity. For example, if you ping any remote server from your MikroTik console, the source IP address is your MikroTik IP address. So, this is an output chain activity.
- Forward processes those packets which are passing through your MikroTik Router. In this case, MikroTik Router is neither source nor destination. In short, when packet passes through MikroTik Router then it is considered as forward chain activity. For example, when your LAN user browses any website, they pass through your MikroTik router. Here, the destination is web server and the source is your LAN user. So, this is a forward chain activity. If you want to block any user who will not get access to any web server, you have to select forward chain property in firewall rule.
The following diagram will show how packets are processed in your MikroTik Router including input, output and forward chain.
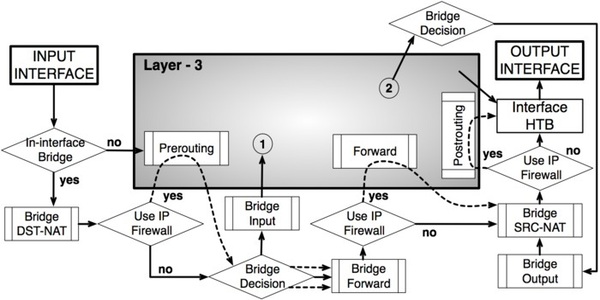
Action in MikroTik Firewall Rule
The action part of MikroTik Firewall Rule defines what to do with the matched condition. The action property is located in Action tab having a lot of self-defined action property values. For example, to drop any packet you can choose drop or to allow packets you can choose accept when condition is matched in conditional part.
Introduction to MikroTik Firewall GUI
Now we will introduce with MikroTik Firewall GUI in winbox software. If you open IP > Firewall menu, you will find seven tabs in winbox Firewall window. Among these tabs, the following tabs are used to create various firewall rules.
- Filter Rules tab contains Firewall rules that block or allow MikroTik traffics. Filter Rules are checked one by one and if any rule is matched with any condition then below rules are not applied for that condition. For example, if you block YouTube for all users but want to allow for a special user, the allowed rule must be placed before the blocked rule. Otherwise the allowed user will go under blocked rule.
- NAT (Network Address Translation) tab contains rules that are related to translate source address or destination address as well as port forwarding. For example, say you have a web server in your LAN and want to access this server from outside of your LAN. Then, you have to create a destination NAT rule to access your web server from outside of your LAN. NAT tab is also familiar to you while creating masquerade rule in MikroTik Router basic configuration.
- Mangle tab contains those rules which are used to mark any packet for further use such as taking different routing decision, blocking any special packet and much more.
- Address Lists tab contains a group of address lists that are used at the time of creating firewall rules such as in a filter rule or in a NAT rule.
- Layer7 Protocols tab contains list of different Layer7 Regular Expressions that are used to block or allow any Layer7 service with Firewall rule.
MikroTik Firewall window in winbox software has briefly been discussed in the above section. In my next few articles, I will explain how to create different filter rules with practical example. Hope you will keep with me.
The basic concept on MikroTik Firewall has been discussed in this article. I hope you have got the basic idea about MikroTik Firewall. However, if you face any problem to understand any terms, feel free to discuss in comment or contact with me from Contact page. I will try my best to stay with you.
Why not a Cup of COFFEE if the solution?


Great