How to Secure MikroTik RouterOS Login Users
MikroTik RouterOS usually sits between WAN and LAN of any network. WAN network is always an insecure network because attackers always try to hack RouterOS so that they can compromise it for their own benefit. If any hacker can compromise MikroTik RouterOS, he can damage RouterOS as well as associated network. As a network administrator, we should always take anti hacking steps to secure MikroTik RouterOS. There are a lot of security tasks those we should take care to harden MikroTik RouterOS. Among these security tasks, we studied how to secure RouterOS login services which are enabled by default. In this article, we will see how to secure MikroTik RouterOS login users from being hacked easily.
Why Do We Need to Harden Login Users?
Because hackers usually try to login RouterOS using username and password if they don’t exploit any vulnerability in RouterOS Firmware. So, we have to harden login users as much as possible so that hackers cannot guess username and password so easily. There are various techniques to harden login users in MikroTik RouterOS. In the following sections we will see some best practices to harden MikroTik RouterOS login users.
Removing Default Username and Password
Default username and password is a common vulnerability to any application because by default any application comes with a default username and password to access it first time so easily. Default username and password is usually known by anyone including hackers and we often forget to remove or modify default username and password. Hackers or any tool (used to login to any application) use default username and password at first to compromise it.
Like other application MikroTik RouterOS comes with a default username admin and black password. As admin user is known to all, it is best practice to remove admin user from RouterOS so that none can use admin user to login MikroTik RouterOS. However, if you wish to keep admin user anyway, don’t forget to set a strong password for admin user. It will also be better to limit admin user access from specific IP addresses.
Making Strong Password for Write and Full Permission Users
Hackers usually do brute forcing using various tools to discover username and password of RouterOS. Tools usually use character combination to find used username and password. So, if we use strong username and password combination, it will take so much time to disclose username and password of RouterOS.
MikroTik RouterOS has three types of login users. These are read, write and full permission user. Read permission users cannot do anything in RouterOS configuration. But can read anything. So, we should be careful enough to set strong username and password for read permission user. Write permission users can alter RouterOS configuration. So, we should be more careful to set strong username and password for the write permission users. It will also be best practice to limit write permission user access from specific IP addresses. Full permission users can do anything in RouterOS. So, we should pay special care to set strong username and password for the full permission users. Never forget to limit full permission user access from specific IP addresses.
Login user can easily be made strong by using long character username and password. It is best practices to use password more than 10 characters long and to use character, numeric and alpha numeric values in password.
Applying User Access from Specific IP Address
MikroTik RouterOS has an awesome feature to limit user access from specific IP address. If we apply IP based user access restriction, user will only be able to login from specific IP addresses. So, user will be secure and hackers will hardly be able to login using user credential.
It is best practice to enable IP based user access for the full permission users and also write permission users. The following steps will show how to apply IP based user access in MikroTik RouterOS.
- Login MikroTik Router using Winbox with full permission user.
- Go to System > Users menu item. User List windows will be appeared.
- Click on Users tab and then double click on any user who will be restricted by IP address. User property window will be appeared.
- From user property windows, click on Allowed Address input box and put your desired IP Address or IP Block from where user will be permitted.
- Click Apply and OK button.
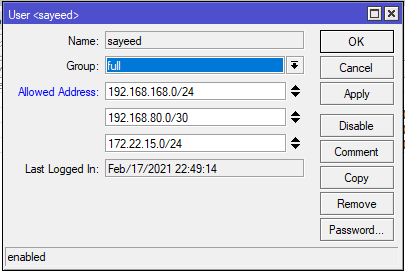
The user will now be restricted and can only be accessible from the desired IP address. Similarly we can enable IP based access for the other users.
Besides enabling IP based user restriction we should be careful enough to restrict login services from specific IP address. Then, MikroTik RouterOS will be more harder but don’t forget to write down applied restriction. If you forget your applied policy, you will never access RouterOS.
How to secure MikroTik RouterOS login users by enabling IP based user access has been discussed in this article. I hope, you will now be able to harden RouterOS login users from the hackers and keep safe. However, if you face any confusion to apply IP based user restriction, feel free to discuss in comment or contact me from Contact page. I will try my best to stay with you.
Why not a Cup of COFFEE if the solution?

