MikroTik OpenVPN Configuration on TCP Port 443 with Windows OS
MikroTik OpenVPN is an amazing VPN solution. IT provides a secure and encrypted VPN tunnel across public network. Unlike PPTP and L2TP VPN Services which are poorly designed and can easily be blocked, OpenVPN can highly be customized and even can be run on so popular TCP Port 443. So, OpenVPN cannot easily be blocked. OpenVPN uses SSL/TLS Certificates. So, OpenVPN Tunnel is a trusted tunnel to send and receive data across public network. OpenVPN is a site to site VPN technology in nature even in NAT network. But MikroTik OpenVPN has limitation to use PPP username and password although a site to site VPN does not require username and password.
The goal of this article is to configure an OpenVPN Server on so popular TCP Port 443 in MikroTik Router and configure OpenVPN Client in Windows Operating System so that a Windows user can connect to a remote office network and can be able to access remote network resources (Servers, Printers etc.) across public network safely.
Network Diagram
To configure OpenVPN Server in MikroTik Router on TCP Port 443, we are following the below network diagram.
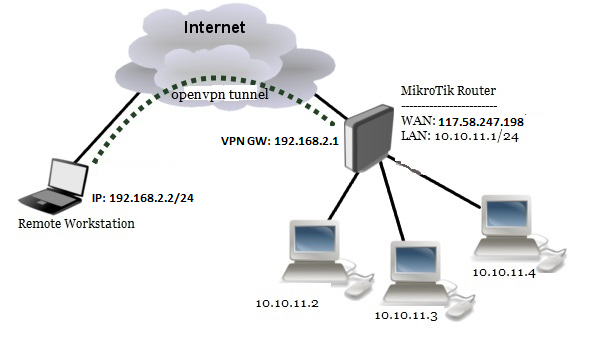
In this network, MikroTik Router (RouterOS v6.46) is connected to internet through ether1 interface having IP address 117.58.247.198/30. In your network, this IP address should be replaced with public IP address. MikroTik Router’s ether2 interface is connected to local network having IP network 10.10.11.0/24. We will configure OpenVPN server in this router and OpenVPN client in a Windows Operating System. After OpenVPN Server and Client configuration, the router will create a virtual interface (OpenVPN Tunnel) across public network where VPN Gateway IP address will be 192.168.2.1 and Client machine will get an IP Address within 192.168.2.0/24 IP Block. We will also declare route in OpenVPN Client so that connected VPN user can access resources of OpenVPN server’s network.
OpenVPN Server and Client Configuration
We will now start OpenVPN Server and Client configuration. Complete OpenVPN configuration can be divided into two parts.
- Part 1: OpenVPN Server Configuration in MikroTik Router
- Part 2: OpenVPN Client Configuration in Windows Operating System
Part 1: OpenVPN Server Configuration in MikroTik Router
According to the network diagram, MikroTik Router is our OpenVPN Server. So, we will enable and configure OpenVPN Server in MikroTik Router. It is assumed that your WAN and LAN networks are working without any issue.
Complete MikroTik OpenVPN Server configuration can be divided into the following three steps.
- Step 1: Creating TLS Certificate for OpenVPN Server and Client
- Step 2: Enabling and Configuring OpenVPN Server
- Step 3: Creating OpenVPN Users
Step 1: Creating TLS Certificate for OpenVPN Server and Client
OpenVPN server and client configuration requires TLS certificate because OpenVPN uses TLS certificate for secure communication. MikroTik RouterOS v6 gives ability to create, store and manage certificates in certificate store. So, we will create required OpenVPN certificate from our RouterOS. OpenVPN Server and Client require three types of certificates:
- CA (Certification Authority) Certificate
- Server Certificate and
- Client Certificate
Creating CA certificate
The following steps will show how to create CA certificate in MikroTik RouterOS.
- From Winbox, go to System > Certificates menu item and click on Certificates tab and then click on PLUS SIGN (+). New Certificate window will appear.
- Put your CA certificate name (for example: CA) in Name input field. Also put a certificate common name (for example: CA) in Common Name input field.
- You will find some optional fields in General tab. You can fill those if you wish. All fields are self-defined.
- Click on Key Usage tab and uncheck all checkboxes except crl sign and key cert. sign checkboxes.
- Click on Apply button and then click on Sign button. Sign window will appear now.
- Your created CA certificate template will appear in Certificate dropdown menu. Select your newly created certificate template if it is not selected.
- Put MikroTik Router’s WAN IP address (example: 117.58.247.198) in CA CRL Host input field.
- Click on Sign button. Your Signed certificate will be created within few seconds.
- Click on OK button to close New Certificate window.
- If newly created CA certificate does not show T flag or Trusted property shows no, double click on your CA certificate and click on Trusted checkbox located at the bottom of General tab and then click on Apply and OK button.
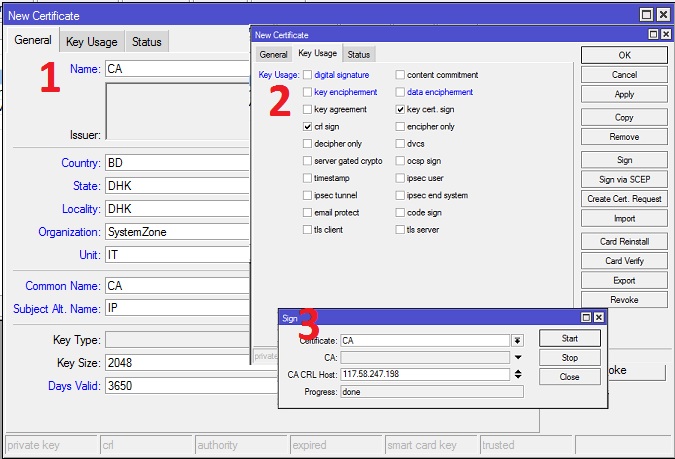
CA certificate has been created successfully. Now we will create server certificate.
Creating Server Certificate
The following steps will show how to create server certificate in MikroTik RouterOS.
- Click on PLUS SIGN (+) again. New Certificate window will appear.
- Put your server certificate name (for example: Server) in Name input field. Also put a certificate common name (for example: Server) in Common Name input field.
- If you have put any optional field in CA certificate, put them here also.
- Click on Key Usage tab and uncheck all checkboxes except digital signature, key encipherment and tls server checkboxes.
- Click on Apply button and then click on Sign button. Sign window will appear now.
- Your newly created Server certificate template will appear in certificate dropdown menu. Select newly created certificate template if it is not selected.
- Also select CA certificate from CA dropdown menu.
- Click on Sign button. Your Signed certificate will be created within few seconds.
- Click on OK button to close New Certificate window.
- If newly created server certificate does not show T flag or Trusted property shows no, double click on your server certificate and click on Trusted checkbox located at the bottom of General tab and then click on Apply and OK button.
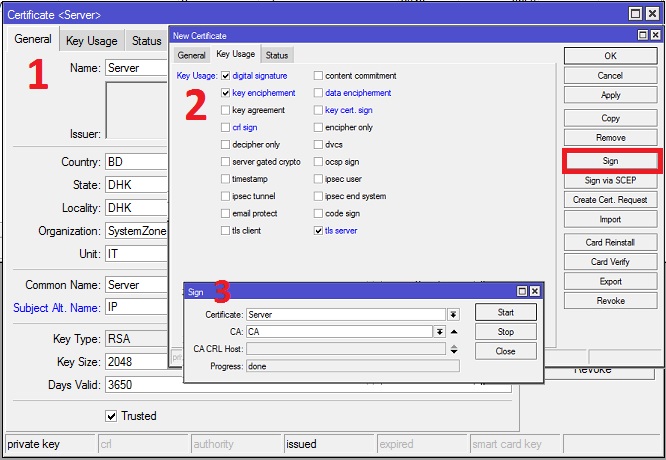
Server certificate has been created successfully. Now we will create client certificate.
Creating Client Certificate
The following steps will show how to create client certificate in MikroTik RouterOS.
- Click on PLUS SIGN (+) again. New Certificate window will appear.
- Put your client certificate name (for example: Client) in Name input field. Also put a certificate common name (for example: Client) in Common Name input field.
- If you put any optional field in CA certificate, put them here also.
- Click on Key Usage tab and uncheck all checkboxes except tls client checkbox.
- Click on Apply button and then click on Sign button. Sign window will appear now.
- Your newly created Client certificate template will appear in certificate dropdown menu. Select your newly created certificate template if it is not selected.
- Also select CA certificate from CA dropdown menu.
- Click on Sign button. Your Signed certificate will be created within few seconds.
- Click on OK button to close New Certificate window.
- Client certificate does not require T flag.
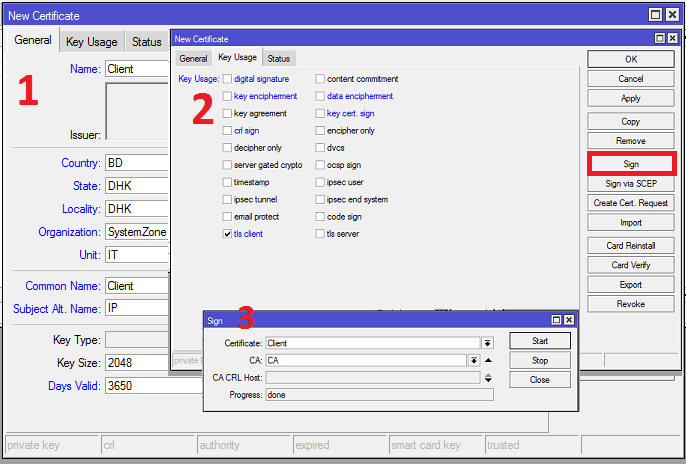
Client certificate has been created successfully. Created and signed CA, Server and Client certificates will look like the following image in Certificates window.
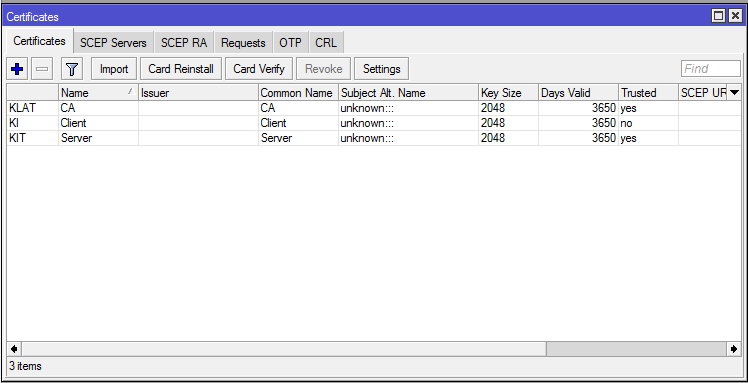
After creating and signing CA, Server and Client certificates, we will now export CA and Client certificates because OpenVPN client will use these certificates.
Exporting CA and Client Certificates
OpenVPN server will use Server certificate from MikroTik RouterOS Certificate store. But client certificate has to supply to the OpenVPN client. So, we need to export client certificate as well as CA certificate from RouterOS certificate store. The following steps will show how to export CA certificate and Client certificate from MikroTik certificate store.
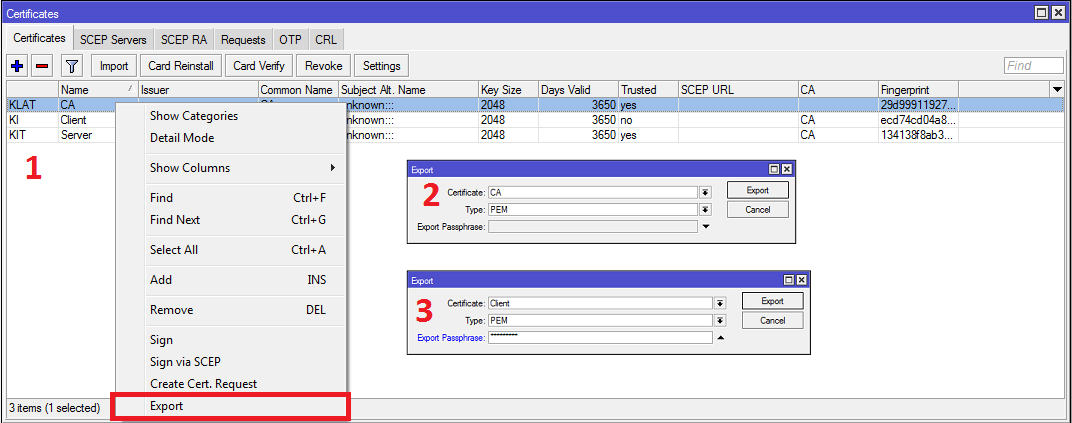
- Select and make Right Click on your CA certificate and then click on Export option. Export window will appear.
- Choose CA certificate from Certificate dropdown menu.
- Click on Export button now. Your CA certificate will be exported and Export window will be closed.
- Similarly, select and make right click on Client certificate and then click on Export option. Choose client certificate from Certificate dropdown menu. Put a password in Export Passphrase input field. The password should be strong enough and must remember because the password has to provide when OpenVPN client will be connected. Click on Export button now.
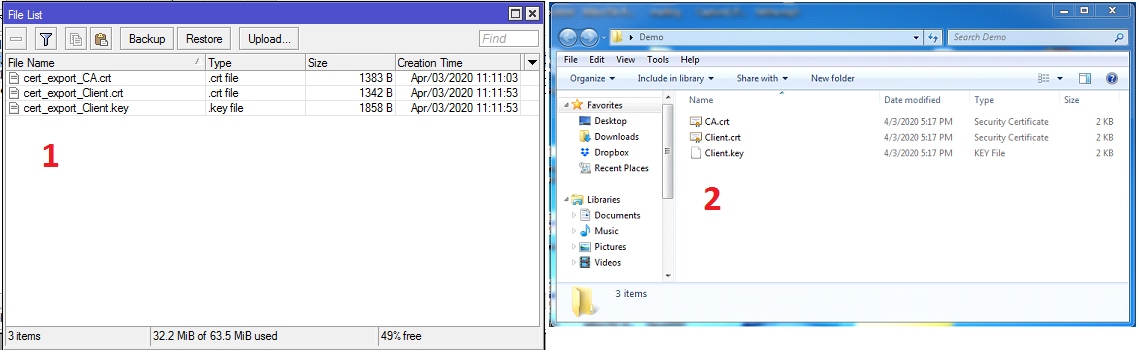
Exported CA and Client certificates with key will be found in Winbox File List window. The following steps will show how to download exported certificates file from File directory.
- Click on Files menu from Winbox menu panel. You will find two certificate files (.crt) and one key file (.key) is exported here.
- Drag and Drop these three files in a folder on your Desktop. We will use these files when OpenVPN Client will be configured.
TLS certificates for OpenVPN Server and Client are ready. Now we will configure our OpenVPN Server in MikroTik Router.
Step 2: OpenVPN Server Configuration in MikroTik Router
After creating TLS certificate, we are now eligible to enable and configure OpenVPN Server in MikroTik Router. The following steps will show how to enable and configure OpenVPN Server in MikroTik Router.
- Click on PPP menu item from Winbox and then click on Interface tab.
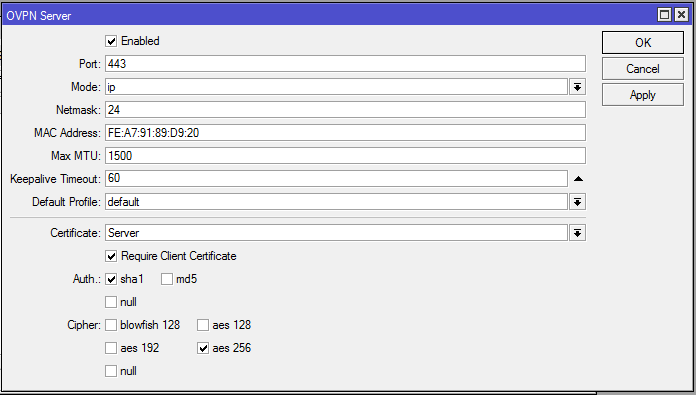
- Click on OVPN Server button. OVPN Server window will appear.
- Click on Enabled checkbox to enable OpenVPN Server.
- Put your desired TCP Port (example: 443) on which you want to run OpenVPN Server in Port input field.
- Make sure ip option is selected in Mode dropdown menu.
- From Certificate dropdown menu, choose server certificate that we created before. Also click on Require Client Certificate checkbox.
- From Auth. Panel, uncheck all checkboxes except sha1.
- From Cipher panel, uncheck all checkboxes except aes 256.
- Now click on Apply and OK button.
OpenVPN Server is now running in MikroTik Router. As MikroTik OpenVPN is limited to use username and password for successful VPN connection, we will now create PPP user who will be able to connect MikroTik OpenVPN Server and get IP information.
Step 3: Creating OpenVPN Users
MikroTik OpenVPN uses username and password to validate legal connection. So, we have to create username and password to allow any user. The complete user configuration for OpenVPN Server can be divided into three parts.
- IP Pool Configuration
- User Profile Configuration and
- User Configuration
IP Pool Configuration
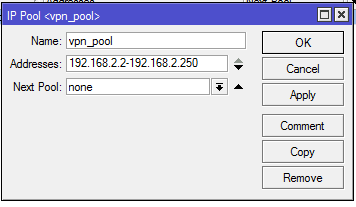
Usually multiple users can connect to OpenVPN Server. So, it is always better to create an IP Pool from where connected user will get IP address. The following steps will show how to create IP Pool in MikroTik Router.
- From Winbox, go to IP > Pool menu item. IP Pool Window will appear.
- Click on PLUS SIGN (+). New IP Pool window will appear.
- Put a meaningful name (vpn_pool) in Name input field.
- Put desired IP Ranges (192.168.2.2-192.168.2.250) in Addresses input filed. Make sure not to use VPN Gateway IP (192.168.2.1) and the last IP (192.168.2.154) because last IP will be used as DHCP Server IP.
- Click Apply and OK button.
User Profile Configuration
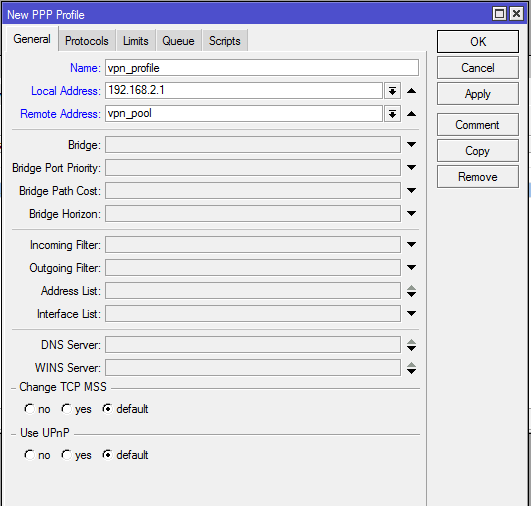
After creating IP Pool, we will now configure profile so that all users can have similar characteristics. The following steps will show how to configure user profile for OpenVPN User.
- From Winbox, go to PPP menu item and click on Profile tab and then click on PLUS SIGN (+). New PPP Profile window will appear.
- Put a meaningful name (vpn_profile) in Name input field.
- Put VPN Gateway address (192.168.2.1) in Local Address input field.
- Choose the created IP Pool (vpn_pool) from Remote Address dropdown menu.
- Click Apply and OK button.
OpenVPN Users Configuration
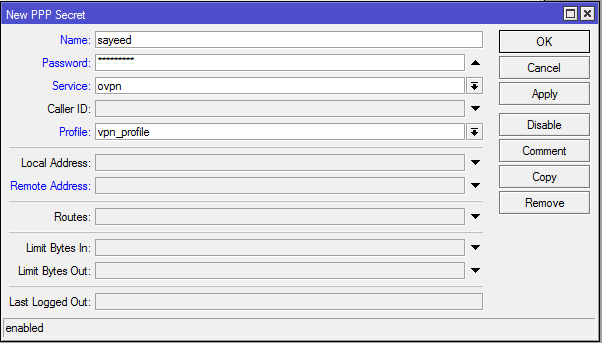
After creating user profile, we will now create users who will be connected to OpenVPN Server. The following steps will show how to create OpenVPN users in MikroTik RouterOS.
- From PPP window, click on Secrets tab and then click on PLUS SIGN (+). New PPP Secret window will appear.
- Put username (For example: sayeed) in Name input field and put password in Password input field.
- Choose ovpn from Service dropdown menu.
- Choose the created profile from Profile dropdown menu.
- Click on Apply and OK button.
We have created a user for OpenVPN Server. Similarly you can create more users that you require.
OpenVPN Server configuration in MikroTik Router has been completed. In the next part we will configure OpenVPN client in Windows Operating System.
Part 2: OpenVPN Client Configuration in Windows Operating System
After configuring OpenVPN Server in MikroTik Router, we will now configure OpenVPN Client. OpenVPN Client configuration can be divided into two steps.
- OpenVPN Client Download and Installation
- OpenVPN Client Configuration
Steps 1: OpenVPN Client Download and Installation
OpenVPN.net provides OpenVPN Client software for all Operating Systems. OpenVPN Client software is found in OpenVPN Community Download page. So, visit to community download page and download OpenVPN Client that matches with your Operating System. I am using Windows 10. So, I downloaded WINDOWS 10/SERVER 2016/SERVER 2019 INSTALLER (NSI) package. At the time of this article, the OpenVPN client installer version was 2.4.8.
If you face any confusion to download OpenVPN client from OpenVPN Community Download, you can Download OpenVPN Client Software Package from this link where I have attached my tested OpenVPN Client Software and Client Configuration file.
After getting OpenVPN Client installer, install OpenVPN client in your operating system following the instructions. Installation process is as simple as installing other software in Windows operating system.
After OpenVPN Client installation, make sure that TAP Virtual Ethernet Adapter has been installed. If it is installed successfully, you will find a new Network Adapter named as TAP-Windows Adapter in Network Connections window.
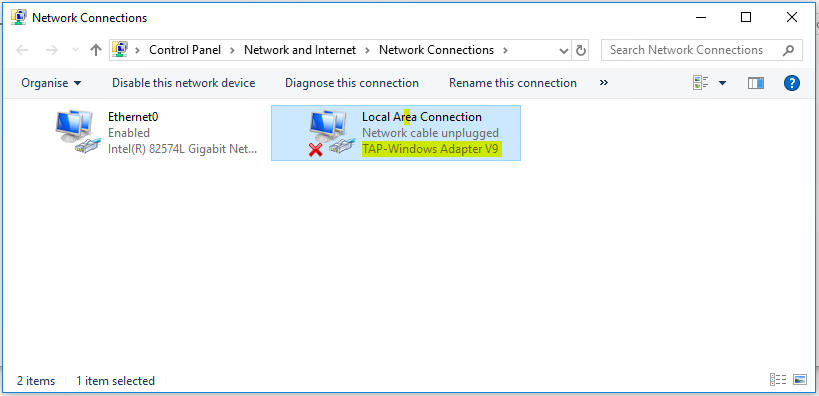
If don’t find this TAP-Windows Adapter in Network Connections panel, uninstall the false installation from Windows Program and Features panel and then download my OpenVPN Client Package where I have attached another TAP-Windows installer and install that installer. I hope you will now find the TAP-Windows Adapter. Without TAP-Windows Adapter OpenVPN Client cannot be able to connect to OpenVPN Server.
Step 2: OpenVPN Client Configuration
After installing OpenVPN client software, we need to configure OpenVPN Client according to our OpenVPN Server requirements. OpenVPN Client configuration file is a UNIX like configuration file. The default OpenVPN configuration directory is C:\Program Files\OpenVPN. This directory looks like the below image.
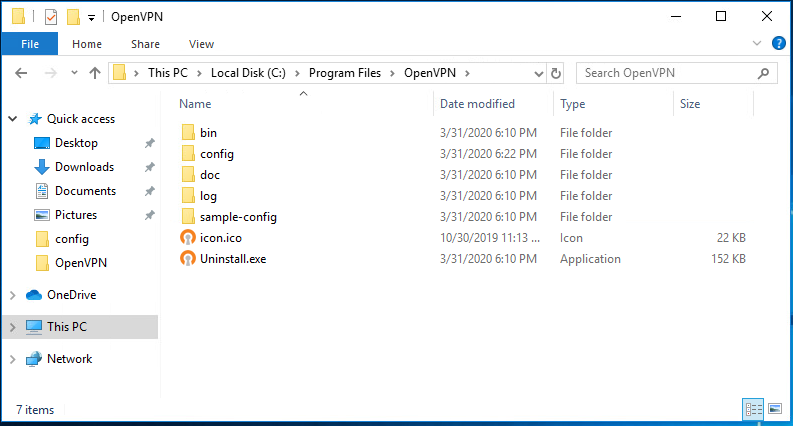
In this directory, a folder named sample-config will be found where a sample OpenVPN Client configuration file named client.ovpn is provided. Copy this sample configuration file into config folder and then open the client configuration file with a text editor such as WordPad, NotePad ++ or any editor that you like. Make sure the editor is opened with administrator privilege otherwise you cannot save the file when you make change.
Configuration Parameters Those We Need to Change
In the client.ovpn file, some parameters are required to change according to our OpenVPN Server configuration. The following parameters are required to change in client configuration file.
Protocol
By default OpenVPN client uses UDP protocol but MikroTik OpenVPN Server supports only TCP protocol. So, enable proto tcp and disable proto udp which may be found at line 36 and 37.
Note: To disable any option just put a semicolon (;) before that option and to enable any option remove the semicolon (;) from that option.
IP and Port
We must specify OpenVPN Server IP and Port in Client configuration file. IP and Port are declared with remote option which may be found at line 42 and the IP and Port should be declared in a line like below. Make sure to change your WAN IP with the example IP (117.58.247.198) and port (443) with your define port.
remote 117.58.247.198:443
SSL/TLS Parameters
In client configuration file, we need to declare CA and Client certificates and Client Key file. These options may be found at line 88, 89 and 90. So, assign ca, cert and key file like below.
ca CA.crt
cert Client.crt
key Client.key
Make sure to rename exported and downloaded ca, client and key file according to the above options and then copy your renamed CA.crt, Client.crt and Client.key files into config directory.
We are not using any server key file. So we have to disable tls-auth option which is enabled by default. The tls-auth option may be found at line 108. So, disable this option by putting a semicolon (;) before it.
Configuration Options Those We Need to Add
There are some options those we need to declare in client configuration file because by default these options are not included in sample configuration file but MikroTik Router requires those options. The following options are required to include in client configuration to work with MikroTik OpenVPN Server properly.
User Authentication
MikroTik OpenVPN Server is limited to work with user verification. So we have to provide username and password with auth-user-pass option. Add this option at the bottom of the client configuration file and declare a file name where username and password are stored like below.
auth-user-pass secret.cfg
Now create a file named secret.cfg in config directory and specify username and password in this file. Username must be declared at the first line and password must be declared at the second line like below.
sayeed
password
Routing Information
By default OpenVPN Client will only be able to communicate with the same network IP Addresses. But remote network resources (Servers, Printers etc.) may have another network. In this case we have to declare routing with route option otherwise OpenVPN Client cannot reach to other network.
For example, Our VPN Gateway Address is 192.168.2.1 and Server network is 10.10.11.0/24. So, to reach this network we have to add route option like below.
route 10.10.11.0 255.255.255.0 192.168.2.1
If you have multiple networks, you have to add multiple route options but each route option per line.
Download Demo OpenVPN Client Configuration File
If you face any confusion to edit the above configuration option, Download OpenVPN Client Configuration File which has been prepared for this article configuration and cross check with your configuration file. Hope your confusion will be reduced.
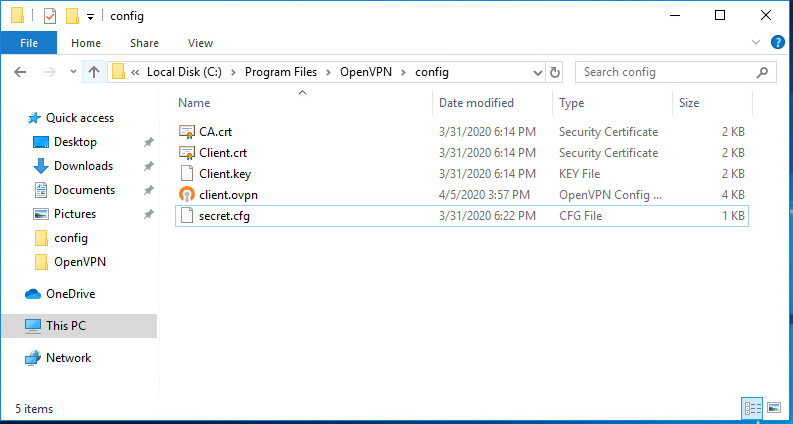
After coping CA.crt, Cleint.crt, Client.key and client.ovpn files, your config directory will look like the below image.
Connecting OpenVPN Client
After completing client configuration, run OpenVPN Client by clicking OpenVPN GUI desktop shortcut icon. You will now find a new OpenVPN icon in Taskbar or System tray like below image.
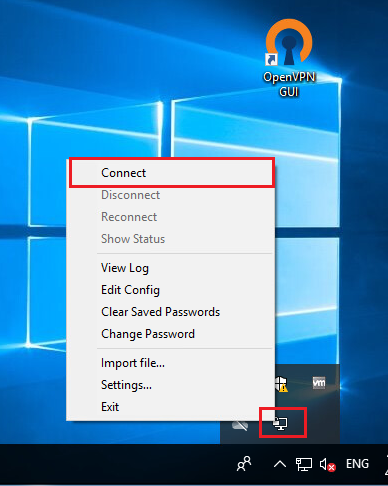
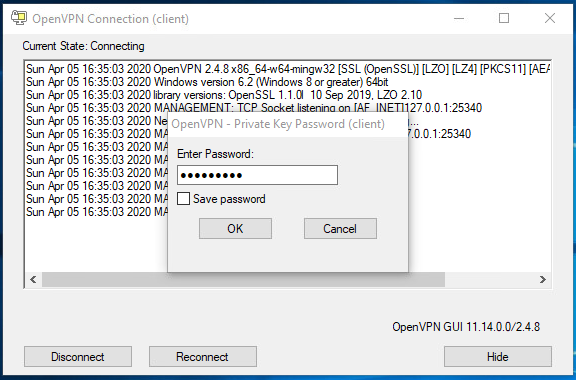
Click mouse right button on this icon and then click Connect option. OpenVPN Connection window will appear and it will ask to put client certificate password that you have entered at the time of client certificate exportation.
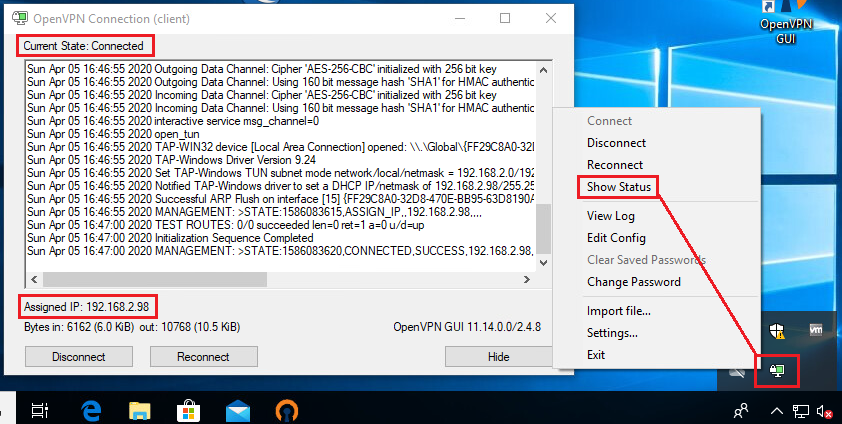
After verifying Client Certificate Password as well as username and password, OpenVPN Client will be connected and an IP address will be assigned to TAP-Windows Adapter. At successful OpenVPN connection, the OpenVPN Client icon will be turned into green.
Now you will be able to access your remote office resources such as File Server, Printers and so on without any issue.
How to Configure OpenVPN Server on TCP Port 443 in MikroTik with Windows 10 Operating System has been discussed in this article. I hope you will now be able to configure MikroTik OpenVPN Server and can be connected across public network from remote location securely. However, if you face any confusion to configure MikroTik OpenVPN Server and OpenVPN Client, feel free to discuss in comment or contact me from Contact Page. I will try my best to stay with you.
Why not a Cup of COFFEE if the solution?

